“The year 2018 will be even more important in terms of security” advocated the Minister of Internal Affairs, Gérard Collomb, at the FIC 2018 – the International Cybersecurity Forum which was held in Lille on January 23rd and 24th. Yet after the Wanna Cry attack, the data leaks at Equifax, at Uber and so on, security issues have made 2017 a busy year in terms of security.
A late awareness
Topics such as “Security & Privacy by Design” or “Secure Data” or even “Move to Cloud” have been talked about for a long time. But where are we now? Has security taken a more important place in projects? Are collaborators aware and conscious of this change in order to integrate it in their daily work?
So many questions that are not yet all resolved. In the case of France and Europe some laws began to arrive in the recent years. We can indeed quote the “Military Programming Law” (LPM) for the “Operators of Vital Importance” (OIV) which are, in France, organisations that have been identified as having vital activities for the country. In Europe, the General Data Protection Regulation (GDPR) focuses on enterprises dealing with Europeans’ personal data as well as the NIS; (Network and Information Security) aiming to reinforce the national capacities in terms of cybersecurity.
2018 begins on the run with Meltdown and Spectre
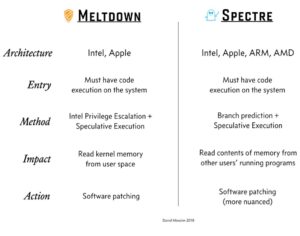
The transition between 2017 and 2018 has started well in terms of cybersecurity: two new flaws affecting almost all processors (CPU) both in servers as well as in computers or phones, have been discovered. These flaws named “Spectre” and “Meltdown” question the architecture of Intel processors in particular, but also those of ARM and AMD.
These flaws were born due to successive optimisations on the processors since the years 1995, in the race to the speed at the expense of the security. Moore’s laws and deduced empirical laws predicted an increase in processors’ speed, but not their increase in terms of security. This summary chart explains the different characteristics of each flaw:
Cybersecurity has become an imperative for businesses
We thought that we had solid and legitimate bases in terms of security, we did not think that the hardware would be affected. What if everything was questioned?
Companies today must adopt a “culture of insecurity” to predict from the design of a system / application / service, a correction process in case they would discover vulnerabilities.
Systems must therefore be dynamic in order to be able to adapt to the discovery of a flaw: patches allow, in most cases, to fix vulnerabilities however they are not included in the conception framework.
At a FIC workshop, speakers highlighted different models for information systems. Indeed, we should go from the “Castle” model (represented by a single barrier at the entrance without any other ways of securing inside) to the “airport” model, or to the citadel one, with a many secure zones inside, adapted to the context, to the exchanges flow and to the already-exisisting assets.
This model is based on the “onion rings” and “DMZ” (Demilitarised Zones) which are network partitions; with more or less important access to the public, in order to gradually protect the IS and the – sensitive – information it contains.
Beware of too fast innovation: The “Hype Cycle”
This is a study done on the evolution of interest in a new technology. The Gartner offers a representation, in the form of a curve for example, on the subjects of the Cloud in terms of cybersecurity.

Source : Gartner, Hype Cycle for Cloud Security, 2017
The first two phases correspond to a craze and therefore a growth of the technology. A concrete example would be “Pokemon Go” who had a peak of “hype” followed by a downfall as violent as its rise.
In terms of security it is precisely in this rise of “hype” of a product or technology that we must not neglect security.
The economic model of the attackers has changed. While 10 years ago, investing a few thousand euros in an attack was madness and was not profitable, we are now talking about millions of euros with increased profits. Motivations have also changed, we are now talking about industrial spying, ransomware, cyber wars … We must remain vigilant and secure as much as possible, integrating security right from the beginning, at the conception phase of projects, will limit risks.